NOTES
- This page provide links to PYTON 3 encryption programs. Notes are work in progress……. PYTHON program to be released.
- The user will need to have installed the latest version of PYTHON 3 from python.org
- PYTHON 3 source code for One Time Pad here: -to be released - otp.py link
- The one-time-pad encryption program adds together a plain text and a key text of similar or greater length.
- The user selects the two texts from the menu. The program produces an encrypted file of the format: n,n,n,n,n,n…… where each 'n' is a number created from adding the ASCII character number of the plaintext character to the ASCII number of the key text character , then a constant subtraction is made from the total.
- The user needs to create their own key files. This can be done by randomly typing from the keyboard, the same number, or greater characters than the plaintext. It is not recommended to use a random character generator,as most computer random-generators are not completely random.
- The user creates two copies of the key files, one for the sender an one for the recipient. The main vulnerability of this particular cypher is the security of these keys, and the user is responsible for the creation and distribution. An agreed published text that is already on the internet, an agreed paragraph of a news item that can be cut and pasted from a web-page, is one example of obtaining a key text without having to possess it.
- The resultant enciphered file can be cut/pasted into an email or appended.
VULNERABILITIES AND SECURITY CONSIDERATIONS
- A possible method of reading the plaintext would be by gaining access to the computers used by either end and locating the key files or plaintexts from that machine, so it is important to delete all plaintext and key files after sending.
- The re-use of a key text can raise the possibilities that a plaintext can be recovered
- Another vulnerability is if the uses selects a key text that can be guessed by a person familiar with their literary preferences.
INSTRUCTIONS For ENCRYPTION
- After installing PYTHON3, and the IDE (Development Environment tool).
- Create a folder on two USB sticks or similar memory devices, and copy the cypher program on to each.
-
Start IDLE program
-
IDLE PROGRAM select window
From the IDLE top-bar menu: FILE: OPEN: then traverse to the folder containing the program and select OPEN: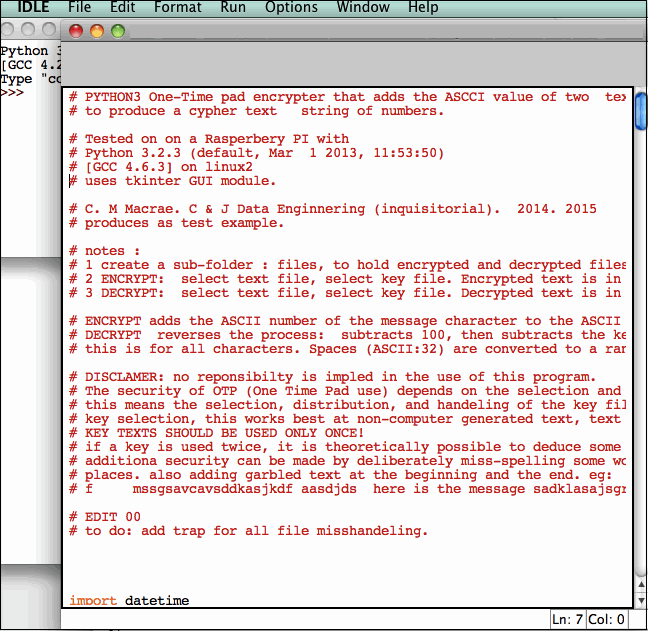
-
Select the RUN button:
-
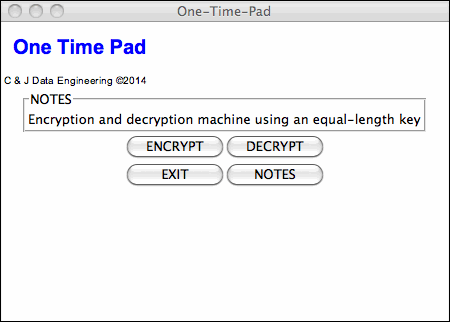
Select ENCRYPT:
-
Select "Select Text File" Button
and traverse to the plaintext file and select OPEN -
Repeat the above, selecting the key file
-
A file of name format: Enc_(Day)_(Month)_(Hour)_(Minutes)_(Seconds)_(Year).txt is created in the XXXX folder
The format is a series of numbers separated by spaces. DO not edit or change the file content, but it may be copied and pasted into another file or email body.81 102 112 149 84 113 133 107 115 60 72 106 104 101 114 130 153 72 126 108 99 116 156 131 126 143 129 117 100 154 125 106 115 114 120 139 60 141 113 118 149 83 121 114 118 115 94 130 135 72 100 106 119 118 134 28 101 103 134 145 117 117 116 154 7 116 138 148 131 104 116 140 117 109 60 105 112 117…….
INSTRUCTIONS For DECRYPTION
…. notes produced so far. --- work in progress
\